Four types of fake key attacks. Each diagram represents Alice
Download scientific diagram | Four types of fake key attacks. Each diagram represents Alice (left), her contacts (right), and an adversary (center). The green lines represent secure connections; the red lines represent compromised connections. Note that in each situation, there may be other pairs of clients communicating securely that are not shown. from publication: Automatic Detection of Fake Key Attacks in Secure Messaging | Popular instant messaging applications such as WhatsApp and Signal provide end-to-end encryption for billions of users. They rely on a centralized, application-specific server to distribute public keys and relay encrypted messages between the users. Therefore, they prevent | Automatism, Security and Server | ResearchGate, the professional network for scientists.
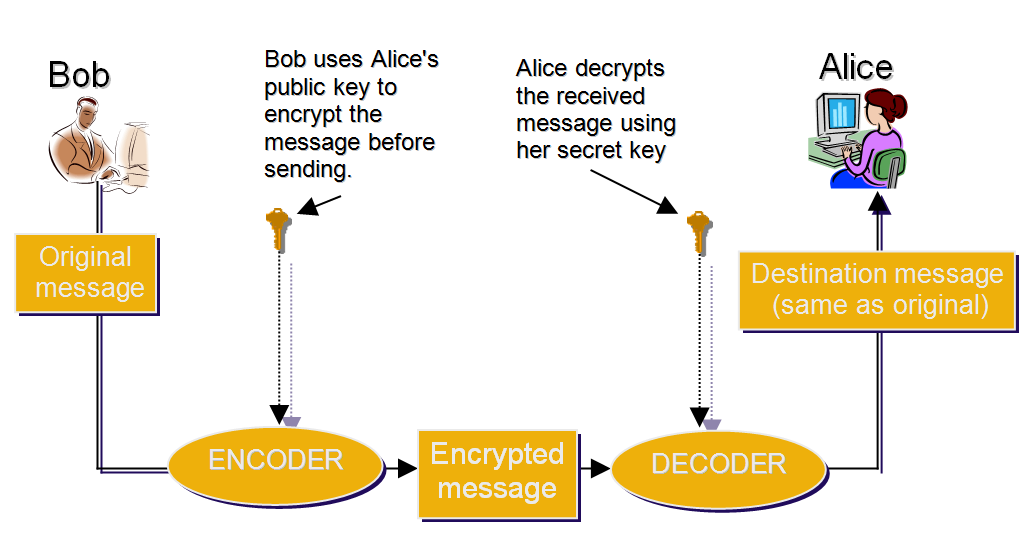
A Deep Dive into Cryptography — SitePoint

Communication scenario of interest. Alice is the transmitter with Bob

The Art of Jean-Michel Basquiat by Fred Hoffman 2017 by jeanmichel - Issuu
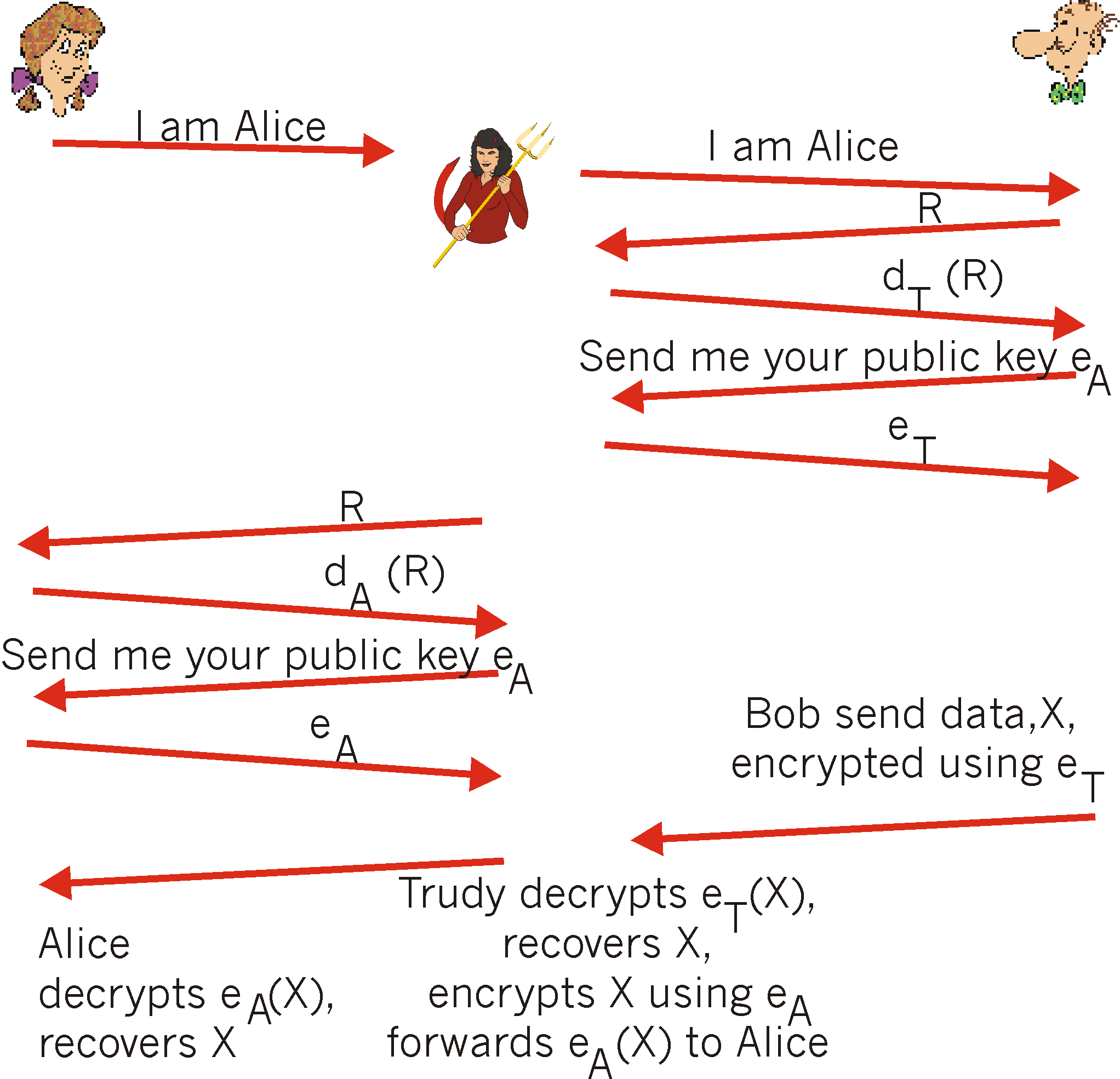
Authentication
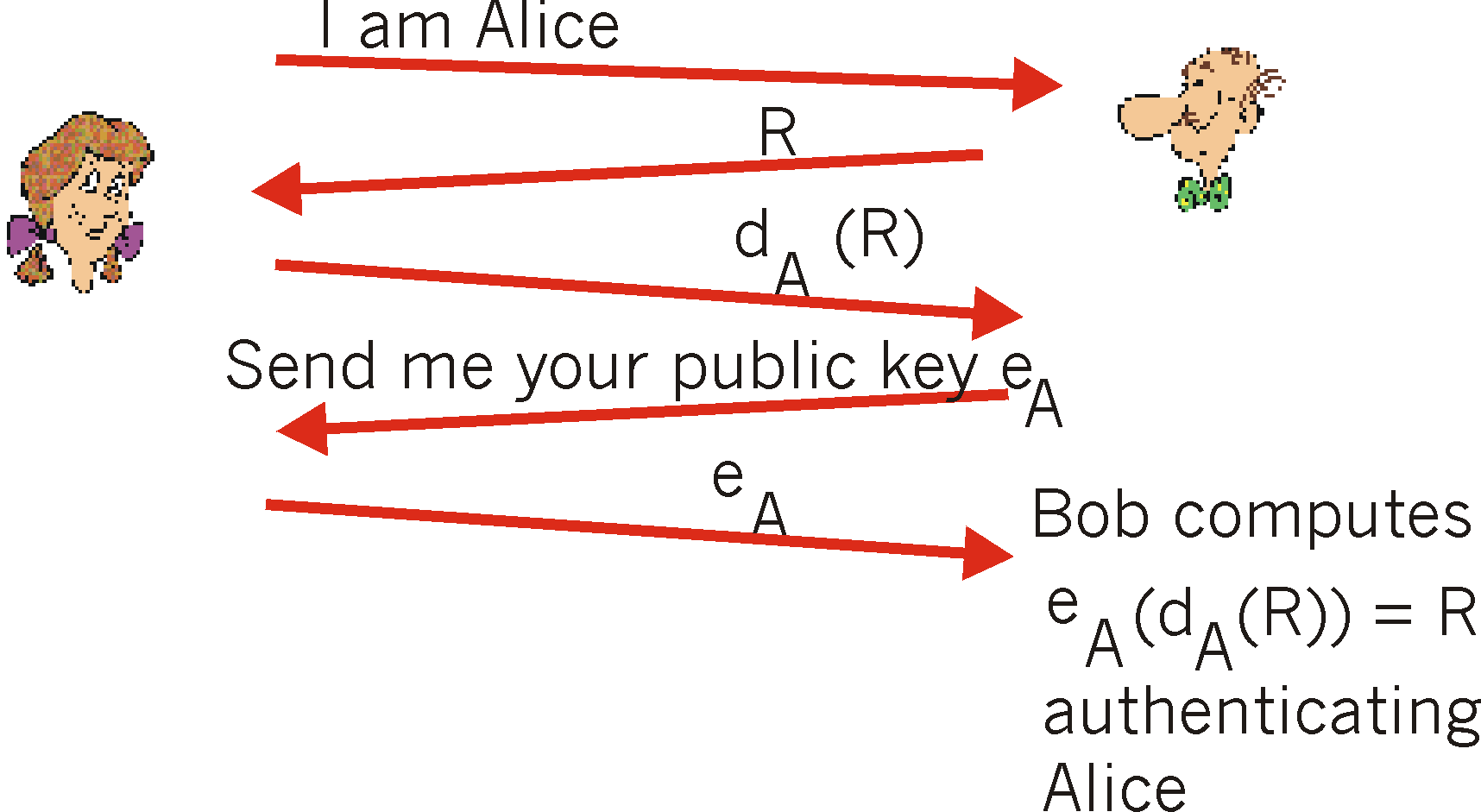
Authentication

PDF) Automatic Detection of Fake Key Attacks in Secure Messaging

Extending loophole-free nonlocal correlations to arbitrarily large distances
Suppose Alice and Bob generate 3 keys and use triple encryption. They encrypt the message using 1st key, then encrypt the result using 2nd key, then encrypt the result again using 3rd

Missing Key: The challenge of cybersecurity and central bank digital currency - Atlantic Council
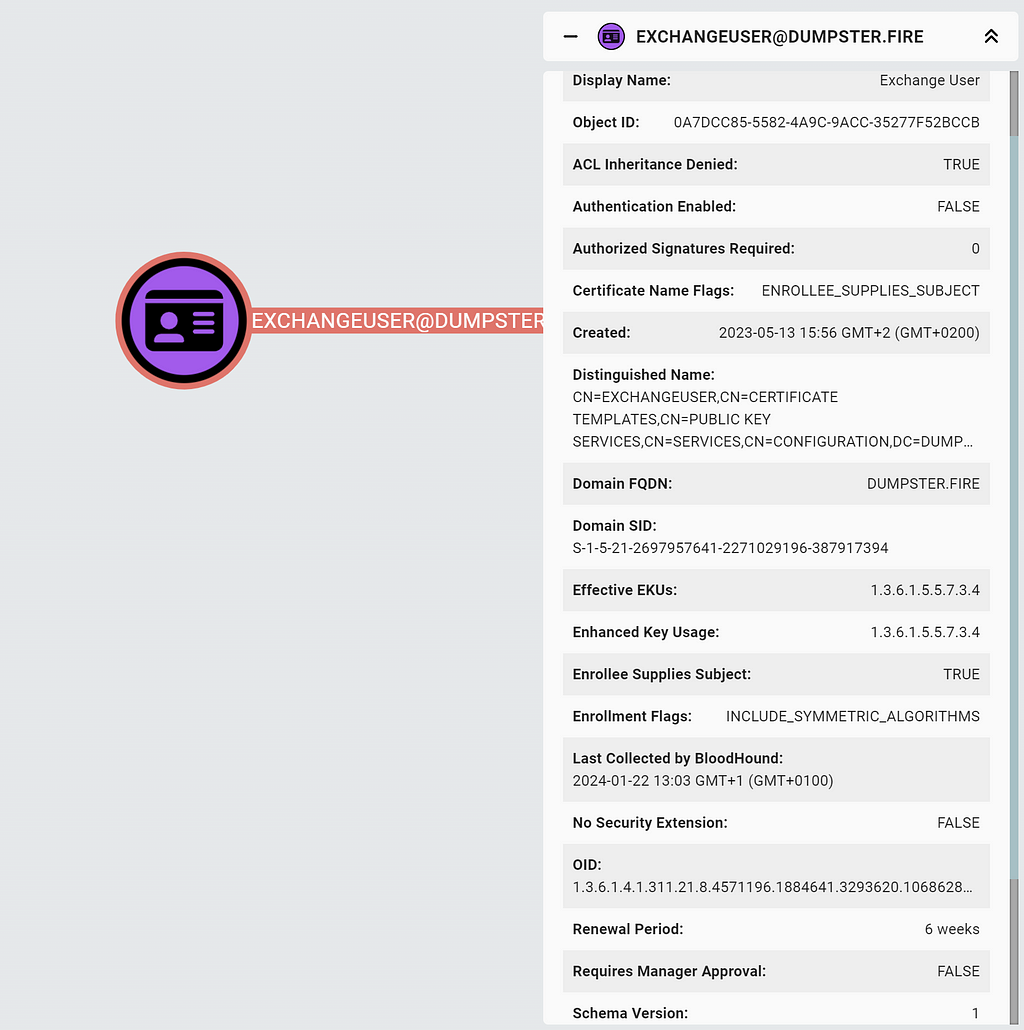
ADCS Attack Paths in BloodHound — Part 1 - Security Boulevard

Mathematics, Free Full-Text

3 Different Types of Cryptography and How Each One Works - History-Computer

Devashish GOSAIN, Postdoc, PhD
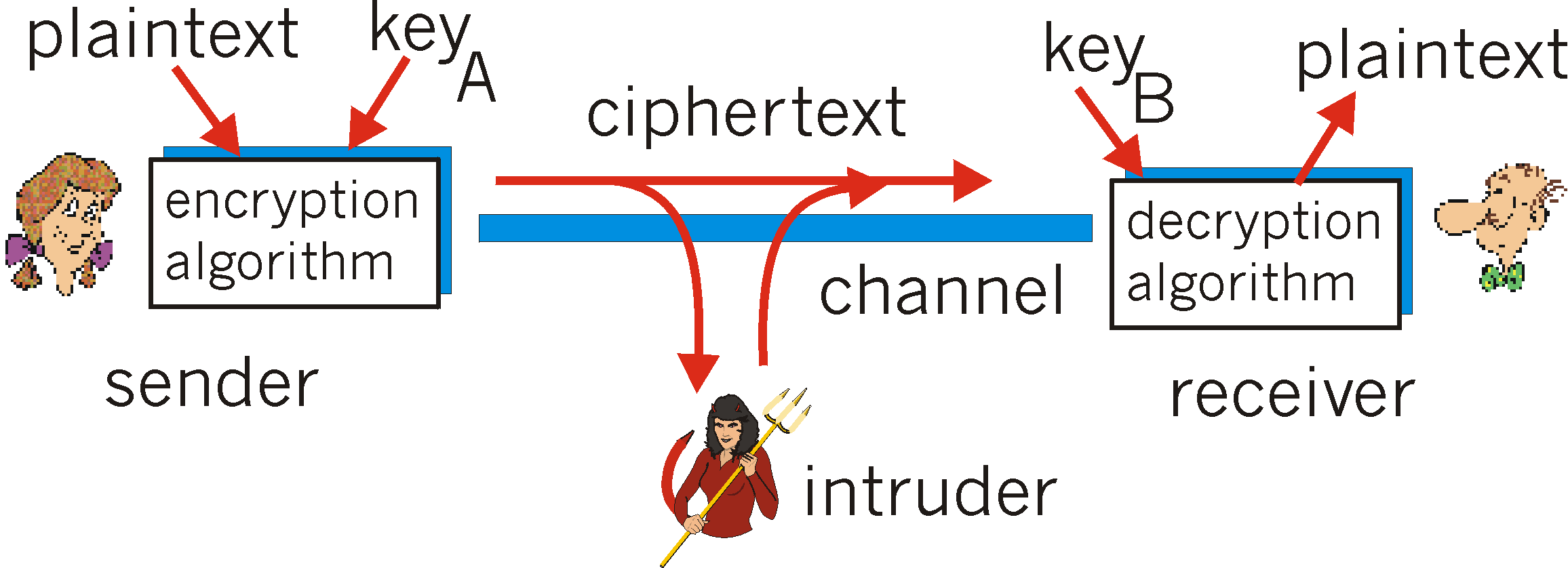
Cryptogrpahy

15.1 Asymmetric Encryption Explained :: Chapter 15. Asymmetric Encryption :: Part III: .NET Cryptography :: .NET Programming security :: Programming
)







